Symptoms
The following record appears every second in /var/log/maillog file:
plesk_saslauthd[5222]: failed mail authenticatication attempt for user '[email protected]' (password len=7)plesk_saslauthd[5222]: failed mail authenticatication attempt for user '[email protected]' (password len=8)postfix/smtpd[14640]: warning: unknown[203.0.113.2]: SASL LOGIN authentication failed: authentication failure
Cause
The server is under brute force attack.
Resolution
Install software which protects the server from the Brute Force Attacks:
Linux
-
Install Fail2Ban according to the article How to install fail2ban on Plesk for Linux.
-
Go to Tools & Settings > IP Address Banning (Fail2Ban);
-
Mark the Enable intrusion detection checkbox and specify the following settings:
-
IP address ban period – the time interval in seconds for which an IP address is banned. When this period is over, the IP address is automatically unbanned.
-
Time interval for detection of subsequent attacks - the time interval in seconds during which the system counts the number of unsuccessful login attempts and other unwanted actions from an IP address.
-
Number of failures before the IP address is banned – the number of failed login attempts from the IP address.
-
-
Activate Fail2Ban service by clicking the Apply button.
-
Go to Jails tab.
-
Mark plesk-dovecot, plesk-horde, plesk-roundcube, plesk-postfix and recidive jails and press the Switch On button to turn the selected jails on.
Windows
To prevent brute force attack, install a tool like Fail2ban, once Fail2ban is only available to Linux systems, for example, ts_block.
In order to verify whether or not the server is vulnerable to this threat, check the following article:
How to test if a server is secured from abuse (Open Relay Test)
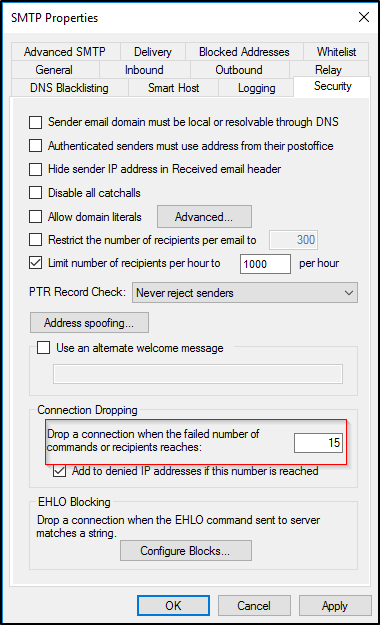
Additionally, to limit brute force attempts, configure MailEnable to block abuser IP:
-
Connect to the server via RDP;
-
Go to Windows > MailEnableAdmin > Connection dropping > Server > Services and Connector > right-click on SMTP > Properties > Security tab: