Juggernaut Security and Firewall
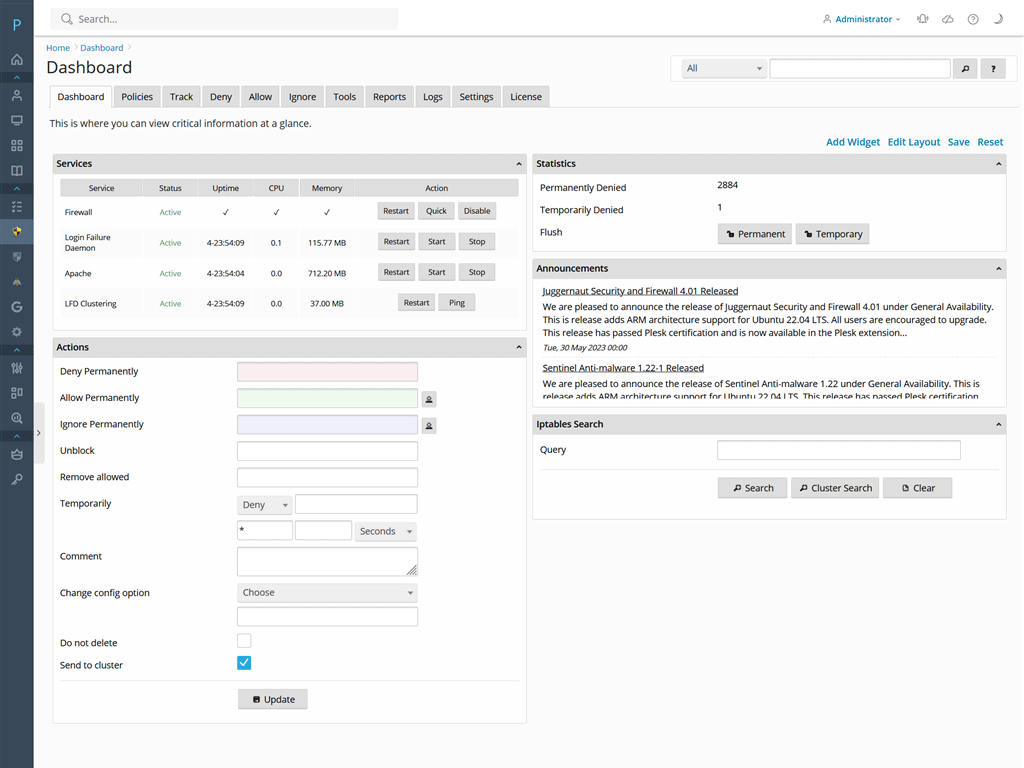
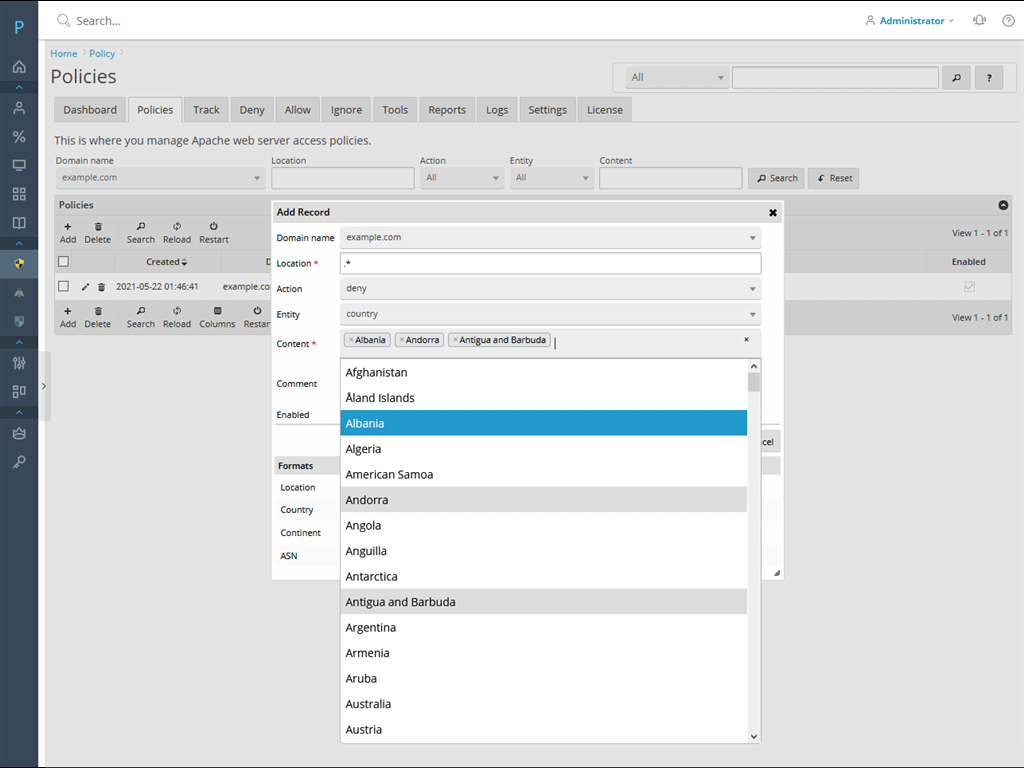
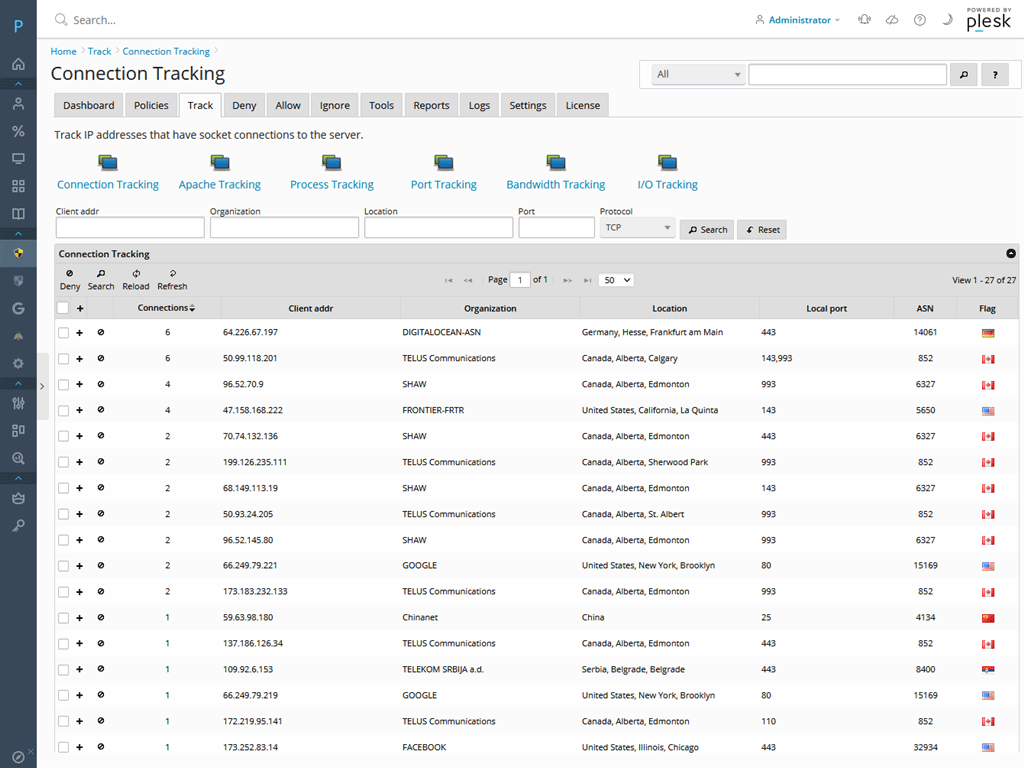
Juggernaut features an SPI firewall, brute-force protection, real-time connection tracking, intrusion detection, dynamic block lists, statistics and reporting, Modsecurity auditing, country blocking, Cloudflare support, and more cutting-edge technology to handle your security needs – all in one security extension.
More Information
https://www.danami.com/products/plesk-extensions/juggernaut-security-and-firewall
Important
- This is a paid extension designed for power users and service providers. Some system administration experience is recommended.
- On Centos/RHEL/Cloudlinux/AlmaLinux the EPEL repository will be enabled.
- The Danami repository will be enabled to install the MaxMind DB Apache module.
- ConfigServer Security & Firewall will be installed on install and removed on uninstall.
- Plesk firewall and fail2ban packages will be automatically removed on install.
Features
SPI Firewall
A next generation SPI iptables firewall that fully supports IPv6 and IP sets. We have pre-configured settings that work on a Plesk server with all the standard Plesk services.
- Full IPv4 and IPv6 support with ip6tables.
- Ipset 6+ support for high performance firewall blocking.
- Allow or deny IP addresses permanently or temporarily (Supports subnets in CIDR notation).
- Create advanced iptables rules for allowing or denying specific IPs or ports.
- Robust command line interface for performing all firewall tasks.
- Enable or disable iptables for specific network cards.
- Enable strict rules to DNS traffic.
- Filter packets for unwanted or illegal packets.
- SYN and UDP flood protection.
- Connection limit protection for protection from DOS attacks against specific ports.
- Flood protection for protection from DOS attacks against specific ports.
- Block traffic on unused IP addresses.
- Whitelist dynamic DNS IP addresses so you never block yourself.
- Search though iptables rules to see if an IP address is blocked.
Brute Force Detection
The login failure daemon complements the SPI firewall and responds to failed logins to block offending IP addresses very quickly.
It continually monitors authentication logs across multiple protocols blocking brute force attacks within seconds.
- Check for login failures against all your server services like SSH, FTP, SMTP, POP3, IMAP, BIND, .htpasswd, Horde, Roundcube, Plesk and Modsecurity.
- We support custom triggers like apache-referrers, apache-useragents, WordPress or php-url-fopen. Block referral spam, bad search engine spiders and WordPress brute-force attacks right on the firewall!
- Add your own custom login failure triggers.
- Add your own custom log files to monitor (supports wildcard patterns).
- Supports both complete blocking or just blocking to the failed application.
- Easily adjust login failures limits per hour for each service before blocking.
- Get a detailed email alert when a trigger is blocked which includes IP location information.
- Convert a temporary block to permanent if the IP address has repeated temporary blocks.
- Block entire netblocks after repeated login failures from the same subnet.
- Ignore specific IP addresses, CIDRs, and countries from being blocked.
- Supports automatic sending of X-ARF reports to the IP addresses that abuse contact.
Real-time Tracking
View all network connections, server processes, Apache connections, bandwidth usage and disk I/O in real-time.
Each IP address is tagged with its location and you can permanently deny an IP with just a few clicks.
- Set the display grid to refresh every few seconds.
- Filter Network connections by protocol, TCP state, and port number.
- Search and sort network connections by connection totals, source, and location.
- Search and sort Apache connections by CPU usage, virtual host, and request method.
- Search and sort processes by CPU and memory usage, process state and the running command.
- Search and sort bandwidth usage by source IP, destination port, transmit and receive bandwidth totals.
- Search and sort disk I/O by process, user, disk read, disk write, swapin, and IO totals.
Intrusion Detection
Monitor system binaries and directories and get an alert when a change is detected. You can even check /tmp and /dev/shm directories for suspicious files.
- Compares md5sums of the servers OS binary application files from the time when the login failure daemon starts.
- Get an email alert when a change is detected.
- Check /tmp and /dev/shm directories for suspicious files.
- Optionally remove any suspicious files found during directory watching and tar them up.
- Add your own custom directories to watch for changes.
Dynamic Block Lists
Add multiple block lists to your server. We support over 100 of the top block list services. Each block list is automatically updated at regular intervals.
- Add block lists like Spamhaus, DShield, BOGON, MaxMind Anonymous Proxy, Project Honey Pot, Fail2ban, OpenBL.org, Autoshun, and TOR to your server.
- Each block lists is automatically updated at regular intervals that you define.
- Easily search and see which block list is denying a specific IP address.
- Add your own custom block lists.
- Add your own global firewall allow, firewall deny, or login failure daemon ignore lists.
Tracking
Track both external and internal threats. Track distributed logins, connection totals, server processes, port scans, and user account changes to the server.
- Track and block distributed login attacks against FTP services.
- Track POP3/IMAP login tracking to enforce logins per hour.
- Track and block total number of connections per IP address.
- Track port scans and block the offending IP address.
- Suspicious process tracking and reporting.
- Excessive user processes tracking and reporting.
- Track SSH and SU logins and get an email alert.
- Track account changes and get an email alert (account created, account deleted, password changed, UID changed, GID changed, login directory changed, login shell changed).
ModSecurity Auditing
View and search through your Modsecurity audit logs. See exactly who is getting denied by your Modsecurity ruleset.
View full HTTP transactions and alerts directly through the Plesk interface.
- View and search through your ModSecurity audit log with ease.
- Fully supports the Plesk and Atomic ModSecurity package.
- View each alert rule id that was triggered in the HTTP transaction.
- View which phase Modsecurity blocked the transaction.
- View the rules that matched and how to whitelist them.
- View the raw HTTP transaction.
- Download the HTTP transaction to your computer.
LFD Clustering
Link all your servers together to share your login failure daemon blocks and configuration changes across the entire server cluster. All server communication is encrypted.
- Share your blocks and configuration options changes across multiple servers.
- Automatically send blocks, unblocks, ignores, and allows to all members of the cluster.
- All communication between servers is encrypted using a secret key that you define.
- Define a master node that can send configuration changes across the cluster.
Country Blocking
Block or allow specific countries or ASNs on the firewall. You can even deny or allow specific ports to specific countries only.
- Whitelist countries that you service from being blocked by the login failure daemon.
- Supports adding ASN numbers when you want to block or allow a specific network only.
- Define how often the Maxmind IP country database is updated.
- Geolocation lookups support both ipv4 and ipv6 IP addresses.
- Legacy systems that cannot run IP sets can ignore smaller CIDR blocks to reduce the number of iptable rules.
Access Policies
Create access policies to deny or allow access to URLs based on the users country, continent, or ASN. The MaxMind DB Apache module provides geo filtering at the web server level.
- Admins can set server wide or domain level policies.
- Admins can create a policy for which countries, continents, or ASNs can access the webmail.
- Resellers and customers can manage policies for their own domains.
- Policies can be easily exported and imported when migrating servers.
- The MaxMind DB Apache module can be enabled server wide or on a per domain basis.
- Provide your customers with geolocation information which they can use with their own PHP code.
Cloudflare Support
Supports interacting with the Cloudflare Firewall using the Cloudflare API.
- Add or remove blocks to the Cloudflare firewall using IP addresses, CIDR, or even two letter country codes (enterprise only)
- Modsecurity trigger automatically blocks attackers on the local firewall and in Cloudflare.
- Command line support for interacting with the Cloudflare API.
- Supports adding multiple Cloudflare accounts.
Statistics and Reporting
We support rich graphs for both server and attack statistics. We organize and present threat data to make it easy to understand where and when attacks are happening.
- Statistical graphs show server load average, CPU, Memory, Network, Disk, Disk write performance, Apache, and MySQL
- Over 50 pre-build reports included and more are being written.
- Export report data to CSV file so you can import into a spreadsheet.
- Reports are as simple as providing a SQL query and outputting to a table class.
- Write your own reports.
Network Information Tools
Perform bulk DNS, Geo, ASN, Ping, Trace, SPF, and DNSBL and Map lookups. Check your servers, domains and IP addresses against multiple DNS and SURBL blacklists.
- Perform DNS, Whois Geo, ASN, Ping, Trace, SPF, and DNSBL and Map lookups
- Supports internationalized domain names.
- Enter your own query or choose from a select list of your servers, domains and IP addresses.
- Add your own DNS servers or randomize nameservers.
- Map lookups use new Maxmind database format fully supporting IPv6.
- Automatically update the Maxmind database at specified intervals.
Messenger Service
The messenger service displays a message to users informing them that they are being blocked in the firewall.
This can help when users get themselves blocked due to multiple login failures.
- Supports redirecting users and displaying text or HTML-based messages over HTTP or HTTPS.
- HTTPS uses your existing SSL certificates on the server, so users get redirected without any security warning.
- The message includes the server hostname and users IP address allowing them to contact you.
- Supports Google reCAPTCHA allowing users to unblock themselves.
- Define what ports to show the HTML message or the TEXT based message.
- Full WYSIWYG editor for editing the HTML message.
- Set maximum concurrent connections allowed to each message service.
Successful Login Auditing
See exactly who is connecting to your server via the console, SSH, FTP or Plesk panel.
Every action performed in Plesk is logged and easily viewable and searchable. View the exact geolocation of each successful login.
- Each IP address is tagged with its location information.
- View the login and logout time and terminal type for each successful login.
- Easily block compromised accounts with just a few clicks.
AbuseIPDB Support
AbuseIPDB is the gold standard for abuse reporting and is used by some of the largest hosting companies worldwide. AbuseIPDB block lists get updated automatically, so your server always has the most up to date threat information.
- If an attack occurs on a server with the block reporting enabled, it will be reported back to AbuseIPDB which will add it to their block lists once it has reached a certain abuse confidence threshold.
- The strength of AbuseIPDB is that every server is sharing attack information. With every new user, abuse reporting gets more accurate, and the defense network grows stronger.
- Easily report abusive IP addresses engaging in hacking attempts or other malicious behavior and help fellow sysadmins.
- Easily check the report history of any IP address to see if anyone else has reported malicious activities.
Multi-Language Support
- English
- Deutsch
- Español
- Français
- Italiano
- Magyar
- Nederlands
- Polski
- Português
- Русский
- Türkçe
- Svenska
- 中文
- 日本語
Supported Operating Systems
- AlmaLinux 9.x
- AlmaLinux 8.x
- CloudLinux 9.x
- CloudLinux 8.x
- Debian 12.x
- Debian 11.x
- RedHat Enterprise Linux 9.x
- RedHat Enterprise Linux 8.x
- Rocky Linux 8.x
- Ubuntu 24.04
- Ubuntu 22.04
Supported VPS
- KVM
- Xen
- Vmware
- HyperV
Supported Plesk Versions
Plesk Obsidian 18.0.62+
Third Party Software
ConfigServer Security & Firewall (csf)